This post is automatically translated with LLM. The translation content has NOT been reviewed and may contain errors.
Just a few days ago, HE.NET Tunnelbroker's French server experienced an outage. When I configured my Kimsufi server, I assigned the native IPv6 addresses to ESXi for exclusive use (as described in this article), leaving pfSense with only native IPv4 and obtaining IPv6 addresses through Tunnelbroker. Consequently, all virtual machines on the server lost IPv6 connectivity. More critically, since I had set up a NAT64 service on the server following this article, and configured pfSense's DNS resolution to prioritize Google DNS's NAT64 servers (2001:4860:4860::64 and 2001:4860:4860::6464) with IPv4 as fallback, DNS resolution almost completely failed due to the IPv6 outage combined with pfSense's long DNS timeout settings.
To prevent such cascading failures from recurring, I plan to use multiple Tunnelbrokers for mutual backup and configure pfSense's Multi-WAN Failover feature. This will ensure immediate failover to alternate Tunnelbrokers if one fails, maintaining uninterrupted IPv6 connectivity.
Setting Up Additional Tunnelbrokers
A current list of operational Tunnelbrokers can be found on the Wikipedia page: List of IPv6 tunnel brokers. Among these, I successfully registered with HE.NET, IP4Market, and NetAssist. Note that NetAssist's server, while previously functional, is now consistently unavailable.
IP4Market is a Russian website with an interface in Russian, but registration can be completed seamlessly using Google Translate.
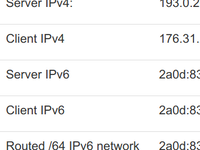
After registration, you'll receive server and client IPv4/IPv6 address information (IPs truncated in screenshot below):
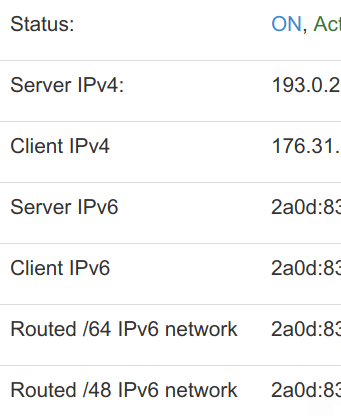
Next, create the tunnel in pfSense. Under Interfaces > Assignments > GIFs, add a GIF tunnel (IPs truncated):
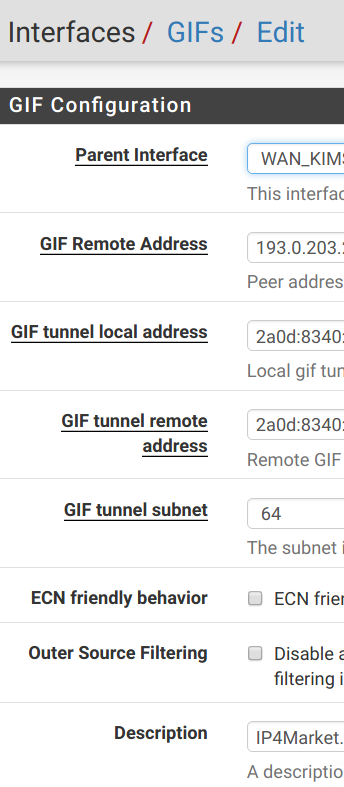
Then assign this tunnel as an interface. Under Interfaces > Assignments, add the newly created tunnel and enable it in the interface settings:
Verify tunnel connectivity by pinging the remote endpoint under Status > Gateways.
Configuring Multi-WAN Automatic Failover
To enable automatic failover when a tunnel fails, navigate to System > Routing > Gateway Groups. This feature allows grouping multiple gateways (including tunnel endpoints) for load balancing or failover.
Add a gateway group and prioritize the tunnel gateways by assigning them Tier 1, Tier 2, etc. Set the Trigger Level to Member Down:
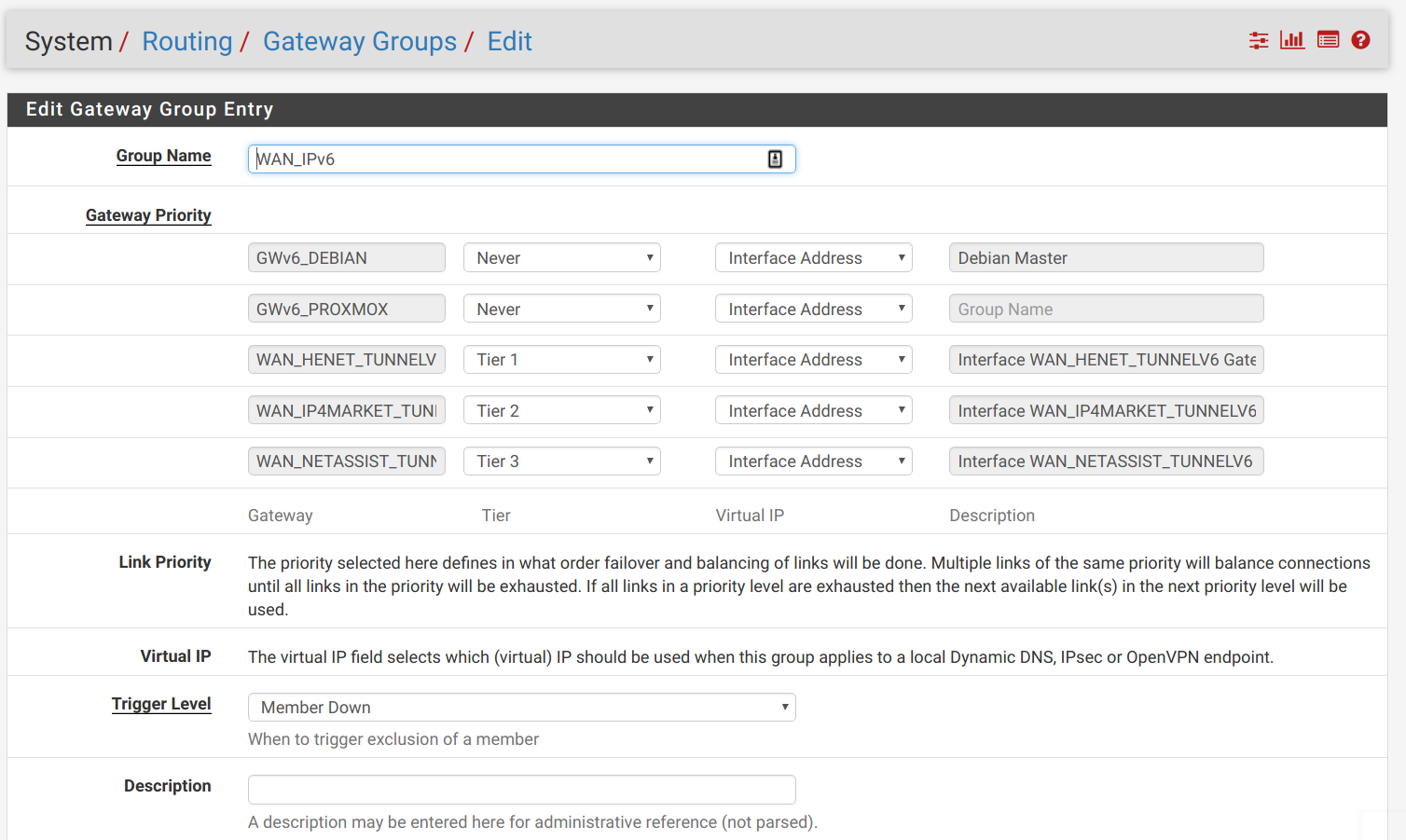
However, if you set this gateway group as the default route, you'll notice that when the primary gateway fails, internal machines still cannot access IPv6 despite the gateway group switching. This occurs because LAN devices typically obtain IPv6 addresses from the primary gateway's pool (e.g., HE.NET). Alternate Tunnelbrokers (like IP4Market) won't recognize these addresses and will block traffic. Even if packets pass through, return traffic would be routed to the offline primary gateway.
The solution is pfSense's NPt (Network Prefix Translation) feature, which performs 1:1 mapping between IPv6 subnets. Here, we map HE.NET addresses to IP4Market's address pool to ensure recognition and forwarding.
Under Firewall > NAT > NPt, add an entry to map LAN addresses to IP4Market's provided subnet:
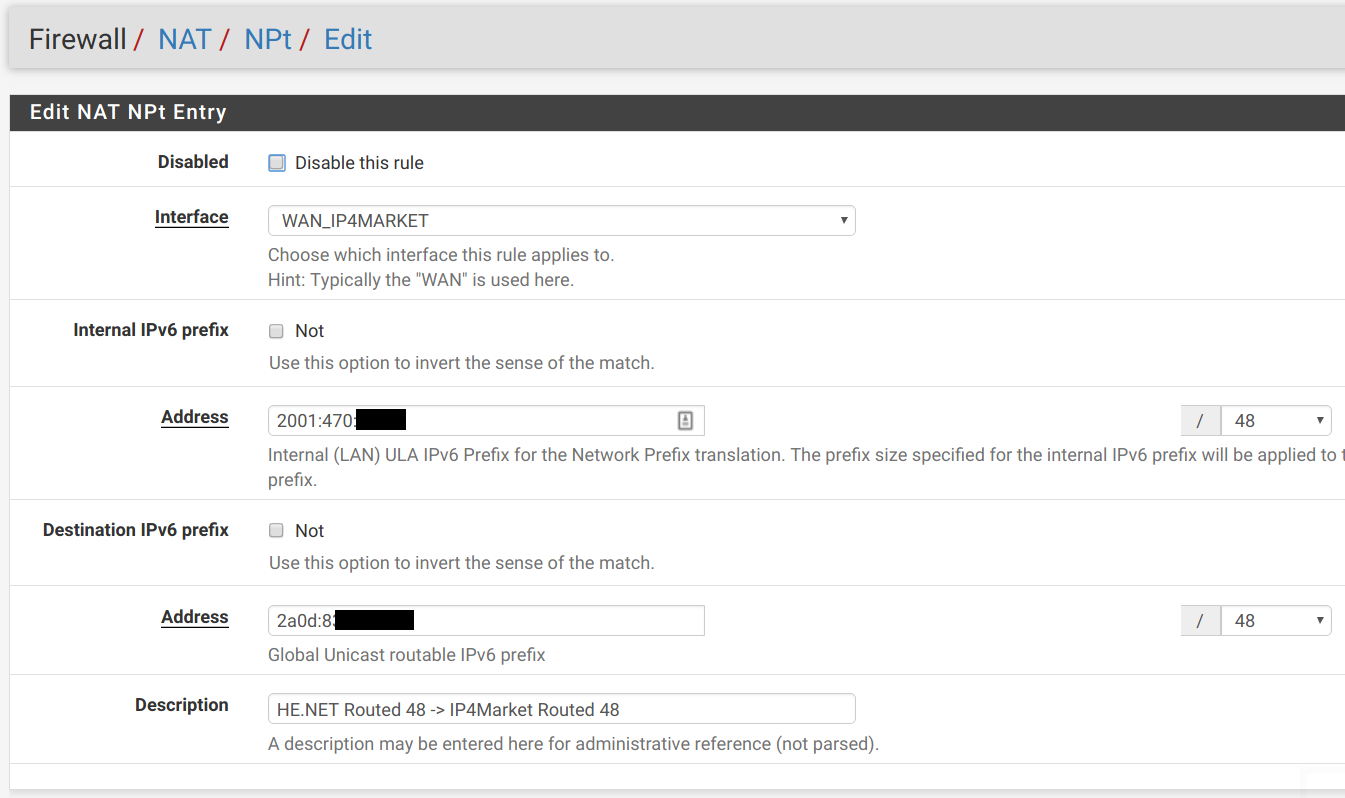
LAN machines can now access the internet via IP4Market's Tunnelbroker.