Our school organized a RoboMaster team and planned to attend the competition this year. Since we are all new students at a new campus, we do not have any reference materials available from previous students, and we have to figure out bugs after bugs on our own. This post describes some of the problems we met during software development. Hardware: RoboMaster Official Development Board MCU Model: STM32F427IIHx Software: ChibiOS 18.2.0 Board Has 12 MHz HSE Clock Instead of Commonly Seen 8MHz The pitfall is that neither the manual nor the hardware schematics mentioned the clock frequency. Due to this problem, the actual frequency we programmatically set with STM32CubeMX or other software is much higher than expected. This caused the following problems:...
Setting Up a NAT64 Server
NAT64 is a technology that emerged during the transition from IPv4 to IPv6. It allows IPv6-only devices to access IPv4 networks by mapping IPv4 addresses to a specific IPv6 address range. However, since purely IPv6-capable devices are still uncommon, its current applications in China mainly focus on two areas: For educational network users where IPv4 is charged/rate-limited/volume-capped while IPv6 is free/unlimited, public NAT64 services can help save costs. For iOS app developers, it serves as a testing environment to pass App Store review requirements. We can also set up a NAT64 server on our own router with both IPv4 and IPv6 connectivity by installing appropriate software. Common solutions include Tayga and Jool. Tayga is outdated with its last update dating back to 2011,...
Raspberry Pi 3B Tinkering Notes: Hardware Watchdog
In computing, a "watchdog" refers to a hardware timer designed to restart a computer when it becomes unresponsive (crashes). The computer's operating system must run a program that continuously communicates with the watchdog hardware. When communication is interrupted for a preset duration, the watchdog will forcibly reboot the system by sending a RESET signal or cutting and restoring power, ensuring services running on the computer aren't disrupted for extended periods. During my Raspberry Pi tinkering, I've crashed it multiple times, forcing manual power cycling to restart. Enabling the hardware watchdog feature on the Raspberry Pi can minimize such occurrences. Loading the Driver Thanks to Linux's "everything is a file" philosophy,...
Solving the Raspberry Pi HW CSum Failure Issue
Today when I logged into my Raspberry Pi and ran df to check disk space as usual, I discovered the TF card was almost full. Initially I thought I had misconfigured settings, causing download files to save to the TF card instead of the external hard drive. After troubleshooting, I found that log files under /var/log occupied a staggering 18G of space. Checking the logs revealed continuous error messages like: Jan 25 22:51:15 lantian-rpi3 kernel: [ 22.143274] eth0: hw csum failure ... [original log content unchanged] ... Jan 25 22:51:15 lantian-rpi3 kernel: [ 22.143755] 3fe0: 76f2ace4 7e9b5cc0 76b29dd4 0006ac00 60000010 ffffffff That is, the Raspberry Pi's Ethernet interface was generating massive errors, causing the kernel to continuously output stack traces that bloated the log files....
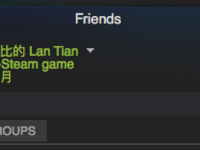
Let ASF Help You "Play" Greedy Moon on Steam
Recently, Greedy Moon (贪玩蓝月) has gained popularity due to its brainwashing advertisements. Many tutorials have emerged showing how to add a custom program to Steam and rename it to "Greedy Moon" to display yourself as playing the game. However, this method requires keeping that custom program running constantly, which can be inconvenient. ASF (ArchiSteamFarm) is a program that simulates game play to farm Steam trading cards. Since it can simulate game play, it can naturally also simulate playing "Greedy Moon" - achieving the effect shown below without any local configuration: To implement this effect, modify the ASF configuration on your host machine running ASF. Open config/[BotName].json and modify these three parameters: "CustomGamePlayedWhileFarming" : "贪玩蓝月" ,...
Raspberry Pi 3B Tinkering Notes: Hardware Random Number Generator
Random numbers play a crucial role in computing. For example, commonly used SSL encryption algorithms heavily rely on random numbers. If the random numbers aren't sufficiently random, attackers might potentially guess them, causing the entire encryption verification system to collapse. However, due to the deterministic nature of computers (where zero is strictly zero and one is strictly one), they cannot generate truly random numbers and can only simulate randomness through complex algorithms. On Linux systems, leveraging its "everything is a file" philosophy, random numbers generated by the Linux kernel from aggregated system data can be read from /dev/random . But because Linux prioritizes security and collects extensive data, the random number generation speed is very slow....
Raspberry Pi 3B Tinkering Notes: BT Download and Policy Routing
Let's get straight to the point this time. (Actually, I'm not sure how to start.) Installing Transmission for PT As a compact computer that can freely connect to various sensors, the Raspberry Pi offers high playability. Even if you don't want to connect a bunch of sensors to the GPIO (or like me, think additional sensors are temporarily unnecessary), you can leverage its low-power characteristics to run it 24/7 for tasks that don't require heavy CPU computation but take a long time to complete due to other factors—like... background downloading. My university has an intranet PT (Private Tracker) site. A PT site is a platform for releasing BT seeds, but it adds user management features on top of traditional BT. By restricting client types and enforcing upload ratio requirements,...

Raspberry Pi 3B Tinkering Notes
During the National Day holiday, I purchased a Raspberry Pi 3B and a bunch of sensors from Taobao to start some projects. Due to holiday shipping delays, all components arrived piecemeal days after the vacation ended. First, a photo of the completed setup: I ordered from five different stores: Raspberry Pi 3B (with case, fan, heatsinks, power supply) SanDisk 32GB TF card Raspberry Pi sensor kit (3.3V compatible, 16 sensors total) 5-inch 800x480 touchscreen DS3231 RTC module and GPIO pin labels (purchased later) Raspberry Pi Unit The Pi 3B arrived first. However, the TF card hadn't arrived yet, leaving the Pi unusable. I proceeded to assemble the case and cooling system. Encountered an issue: The case's internal support pillars were misaligned....
Building Your Own IPv6 Tunnel with ZeroTier One
Preface Most ISPs in China do not provide IPv6 addresses to users, except for the Education Network. However, the IPv6 service on the Education Network is highly unstable (possibly specific to my institution), and once you leave campus, IPv6 becomes unavailable, which is quite frustrating. One alternative is using HE.NET's tunnel service . After SixXS shut down, they are currently the largest remaining IPv6 tunnel provider, and their service is completely free. However, their service isn't suitable for home network environments in China, as home networks typically have dynamic IPs, and some ISPs have started using large-scale NAT to save costs, preventing users from obtaining independent IPs and causing conflicts within the same internal network....
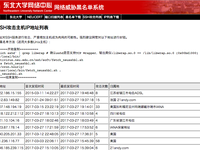
Using the SSH Blacklist System of Northeastern University Network Center
The Network Center of Northeastern University provides an SSH blacklist on its official website, which records IP addresses detected using port scanning tools on SSH ports. This system appears to be based on statistics collected from their own honeypot servers. They also offer a downloadable hosts.deny file corresponding to the blacklist, allowing users to automatically update the SSH blacklist and block these scanners (preventing them from logging in) using scheduling tools like cron. It's unclear exactly when this system was implemented, but it has been operational for at least two years. Additionally, the blocking duration for these IP addresses appears to be 60 days from their last detection. Usage method: Install cron on your server and run the following commands to set up the script:...