This post is automatically translated with LLM. The translation content has NOT been reviewed and may contain errors.
The Network Center of Northeastern University provides an SSH blacklist on its official website, which records IP addresses detected using port scanning tools on SSH ports. This system appears to be based on statistics collected from their own honeypot servers. They also offer a downloadable hosts.deny file corresponding to the blacklist, allowing users to automatically update the SSH blacklist and block these scanners (preventing them from logging in) using scheduling tools like cron.
It's unclear exactly when this system was implemented, but it has been operational for at least two years. Additionally, the blocking duration for these IP addresses appears to be 60 days from their last detection.
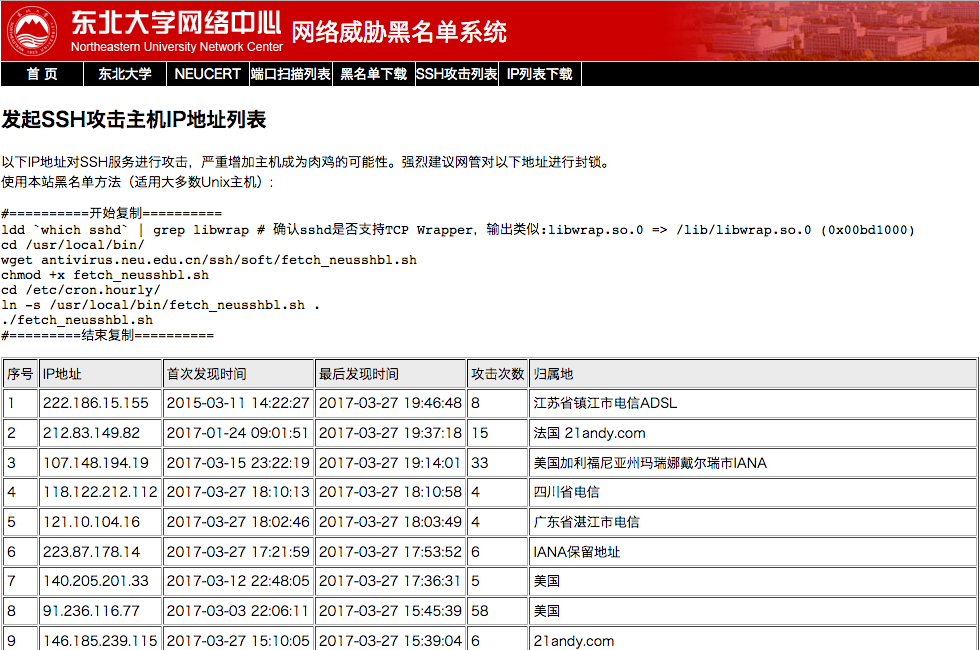
Usage method: Install cron on your server and run the following commands to set up the script:
ldd `which sshd` | grep libwrap
cd /usr/local/bin/
wget antivirus.neu.edu.cn/ssh/soft/fetch_neusshbl.sh
chmod +x fetch_neusshbl.sh
cd /etc/cron.hourly/
ln -s /usr/local/bin/fetch_neusshbl.sh .
./fetch_neusshbl.sh
This script will connect to the Northeastern University Network Center servers hourly, download the latest hosts.deny file, and apply it to your system.